Full Armor is a leader in
Cyber Security
and in
System & Group Policy Management
Learn More
Full Armor can help you secure and manage your IT resources. Schedule a demo!
Since our founding in 2000, we've licensed our technology to companies including Microsoft, Citrix, NetIQ, LogMeIn, F5 Networks, and others. More than 5 million users and 1500 organizations rely on technology developed by Full Armor.
Whether on-premise or in the cloud, Full Armor helps Fortune 1000 companies secure and manage their IT resources.
Leading-edge Solutions to Modern Challenges
AD Bridge
Extend Identity & Configuration Beyond Active DirectoryLearn More

SSHepherd®
Remove the Attack Surface for SSH, RDP or any TCP/IP ApplicationLearn More
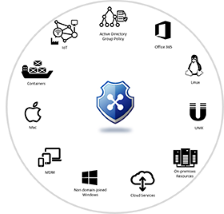
Universal Policy
Group Policy Management Repository - Delegate, Analyze, DeployLearn More
No one wants to become the next cyber breach headline. Let Full Armor help you avoid the limelight.
Secure ALL Users and Devices
Full Armor's innovative technology empowers you to manage users and devices across Windows, Linux, Unix, and Mac.Remove the Attack Surface
Completely remove common attack surfaces leveraged by hackers.On-premise. Cloud. Hybrid.
Manage all your resources, whether on-premise, cloud, or hybrid.Intuitive Web Console
Create, deploy, monitor, and enforce your desired settings through a Single Pane of Glass.



