SSHepherd®
Remove the Attack SurfaceLayered and Complementary Security Practices are Key to Securing Your Network
VPNs and Firewalls are a necessary piece of your perimeter security but this is not enough. Protecting your resources inside the perimeter is a vital piece of your defense.
Preventing unauthorized access to your critical systems, auditing activity during remote access sessions, mitigating risk of data loss, and good cyber hygiene are key to most security compliance guidelines like NIST, CIS, CERT and all others.
Are your assets actively listening for inbound connections?
Are you certain you know who has access to SSH and RDP on your systems?
Do you know if your user credentials are included in the millions already stolen?
Are your SSH keys already compromised?
Have you checked your logs for unauthorized access attempts?
Are you prepared to prove the Who, What, Where and When to auditors?
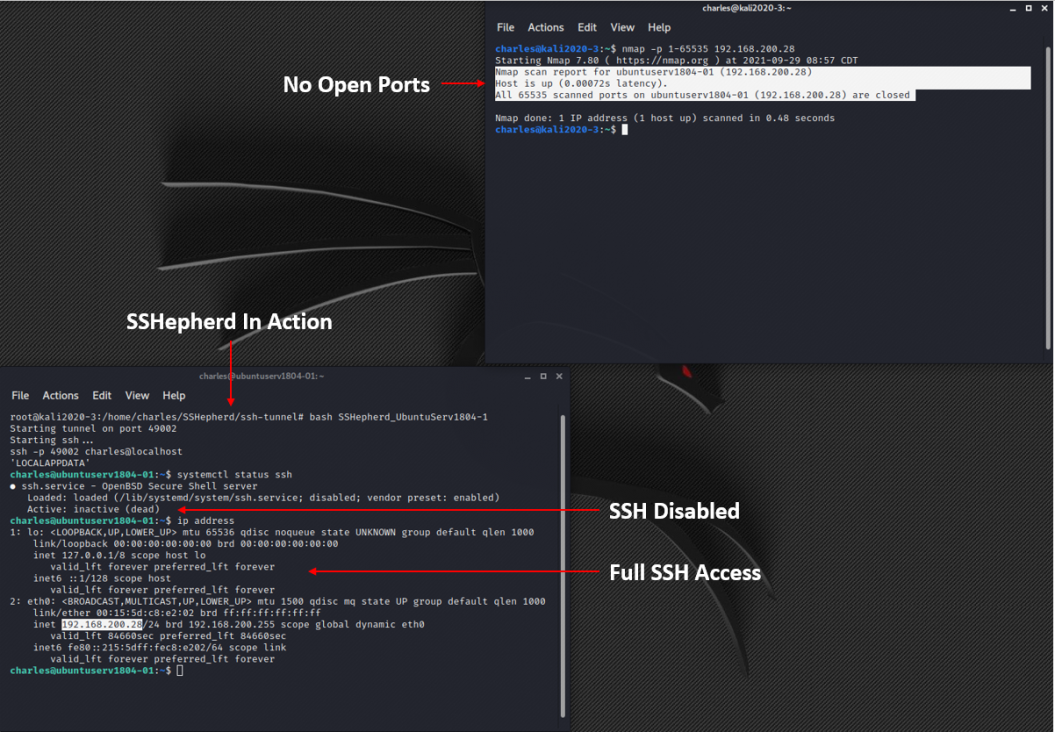
FullArmor SSHepherd® enables you to remove the SSH and RDP attack surface
The Gartner Hype Cycle for Network Security July 14th 2021 report defines Cyber Asset Attack Surface Management (CAASM) as "an emerging technology focused on enabling security teams to solve persistent asset visibility and vulnerability challenges.“
A critical component of CAASM and EASM (External Attack Surface Management) vulnerability management is the complete removal of the SSH and RDP attack surface while maintaining full SSH and RDP capabilities.
Completely Disable SSH
Close All RDP Listening Ports
Block All Inbound SSH & RDP Traffic
Eliminate SSH & RDP From Port Scans
Remove Threat Of SSH Key Sprawl
Prevent Lateral Movement
End SSH & RDP Brute Force Attacks
Maintain FULL SSH & RDP Capabilities